The Future of Proof of Staking-as-a-Service: Exchanges, 0% Fees, and Centralization
After the inception of the World Wide Web/the Internet, numerous up-gradations have happened. Similarly, the same is being seen in the blockchain-run platforms and architectures. As blockchain operates via a decentralized framework, consensus algorithms are the common factor through which a platform or an application operates. This piece focuses on the consensus algorithm Proof of Stake (PoS), how it is perceived as the upcoming potential algorithm which would be able to resolve hurdles from its predecessors. In crux, Proof of Stake aims at doing what the Prof of Work (PoW) was doing but productively, efficiently, and being economically friendly. Unlike in PoW, where miners capability(s) to compute computational issue proves who will receive the prize, in PoS, the one who has more coins/stakes would have higher a probability of getting the prize.
Proof of stake was developed to diminish the computational necessities of proof of work. In PoS, a staker is selected via how much contribution he/she has done. Technically speaking, the stake of a node in a PoS consensus algorithm is the number of digital coins. Another way of seeing these digital coins is, “the coins in cryptocurrency which are held or deposited by the miner staking in the network”. For appropriate functioning of stake-based algorithms, FTS (Follow-the-Satoshi) algorithm is deployed. Some illustrations include Cardano, Tezos. The tokens in the grid/s are indexed and a hash function intakes a seed (a string of erratic length) as an input. Then, an appropriate indexed output is generated through FTS algorithm. Afterward, via an indexed list, a relevant leader is chosen by searching the transaction history. Among numerous benefits of utilizing this algorithmic approach, faster activity validation speed is one of them. If you’re new to the blockchain technology, figure 1 will help in understanding the basics of how blockchain operates. Figure 2 and Table 1 showcases the differences between the functioning of Proof of Work consensus algorithm and Proof of Stake consensus algorithm. In a way, the backbone of security in PoS is network synchrony. The next crucial factor is an incentive mechanism.
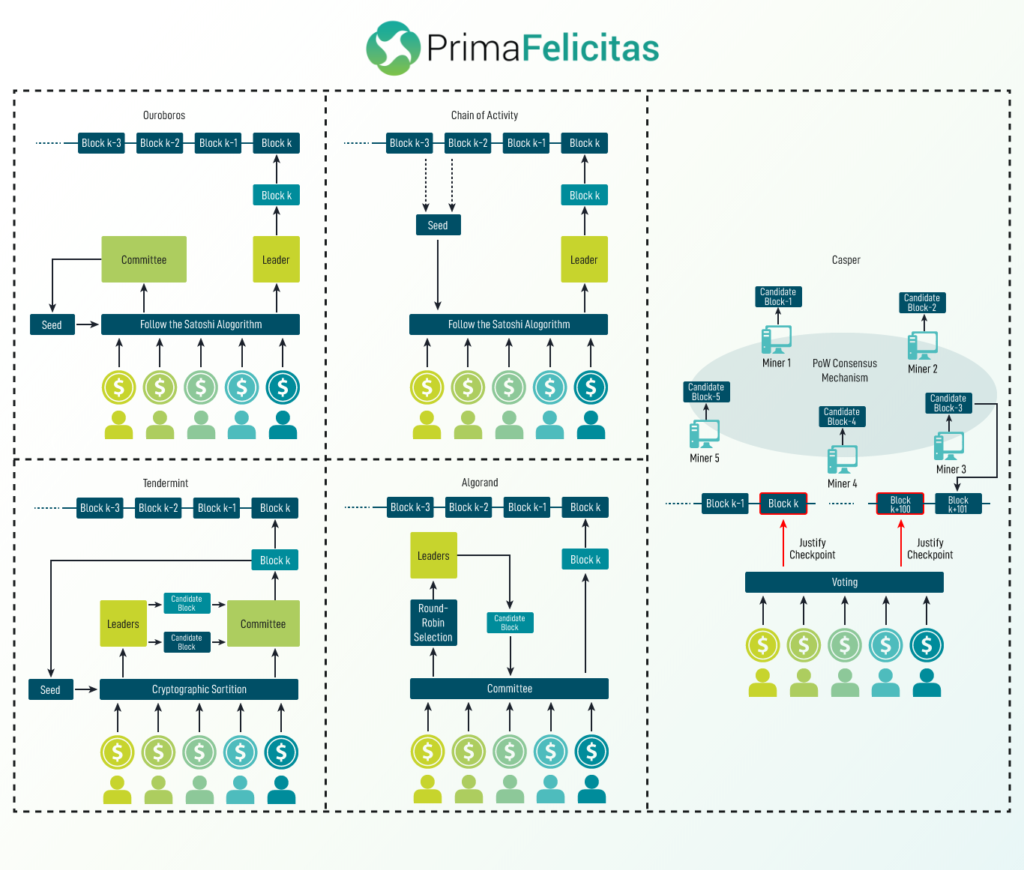
If you’re one of those who are interested to know practical example/s running on the ground, then the infographic placed below showcases five different illustrations. Just to let you know in advance, only their core component (consensus process) is shown in the infographic. Now, let’s scrutinize each illustration’s consensus process. The Casper protocol was built in such a fashion that the PoS framework could function over the PoW protocol/s. The Casper protocol deploys BFT (Byzantine-Fault-Tolerance) protocol for validating checkpoints at each fixed interval. The Ouroboros protocol is a pure-stake-based protocol, meaning the protocol splits time into epchos, and in each epoch, the committee members participate in a 3-phased coin-tossing protocol for building a seed for the FTS algorithm. One edge this protocol (Ouroboros) has is that it consists of low transaction confirmation time and high transaction throughput. One factor that it has been imbibed in various instances is that it has a strong theoretical background for supporting security and incentive compatibility. The chains-of-activity (COA) protocol is slightly distinctive compared to Ouroboros. In COA protocol, the chain gets divided into a group of blocks of length ‘l’, and time is disjoined into each epoch. The hash of each block is utilized for determining the seed of the block. Finally, the seeds of all the bocks built in an epoch are amalgamated to seed the FTS algorithm for opting the successor of epoch leader.
Algorand protocol also operates by employing a committee but it uses a cryptographic sortition mechanism besides FTS algorithm for selecting committee members and leaders. The advantage of deploying sortition is that the selected node isn’t revealed until the proof is submitted, saving the node from getting targeted in advance by a few adversaries. The Tendermint protocol utilizes a BFT voting protocol for validating the block. This protocol is proven to be safe if 2/3 of the voting power is administered by honest participants. Just theoretical knowledge isn’t enough and practical deployment is pivotal for its long-term success. Few areas where Staking as a service is being imbibed are:
- Vehicle sharing
- Data sharing system for IOV networks
- Vehicle trust management system
- Vehicular ad-hoc network
Another aspect through which Prof of Stake is getting implemented is via Cloud Computing as discussed here. According to the proposed prototype, the cloud users wear the hat of peers in the blockchain grid. It’s hypothesized and shown that the provenance feature provides auxiliary security as the Cloud Service Provider (CSP) isn’t able to administer data operations solely by him/her. Instead, the CSP could only manage the resources and authenticate the Blockchain’s consistency.
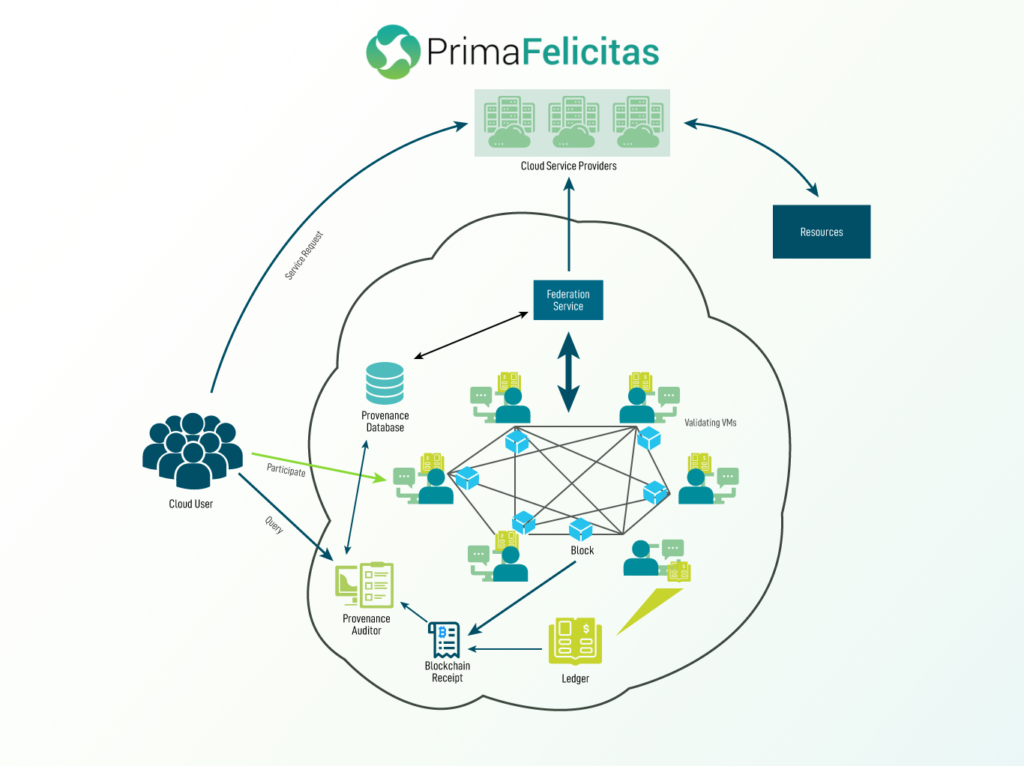
As showcased in the above infographic, each player in the network (CSP, Cloud User…) has a specific role to play, and only after everyone does their job appropriately, the desired outcome is achieved. If you’re someone who has some technical knowledge about blockchain, then just going through the infographic would make you understand the backend functioning quickly.
It should be kept in mind that PoS and Staking-as-a-Service are upcoming areas of research and experimentation. So, there would be numerous illustrations in the coming days. If you want to know more about what’s going on in the blockchain area, visit Primafelicitas to know more about recent, upcoming, and expected updates.
Looking for help here?
Connect with Our Expert for
a detailed discussion
Post Views:
5






